WLAN Standards
WLAN technology has made rapid advancement in the past few years. The reasons
for this are pretty simple: It is very convenient for users; it’s usually less
trouble and cost to deploy (because there are no wires to buy and install); and as
the technology improves, the speeds attainable are pretty respectable, even in
today’s bandwidth-hungry world.
As with any networking technology, some implementations are vendor-proprietary,
but most are compliant with a standard, especially after some time has passed and
the standard is ratified, allowing all the vendors to build equipment that is compliant.
WLANs are defined by a series of standards that are the result of cooperative
work between the International Telecommunication Union-Radio
Communication Sector (ITU-R), the Institute of Electrical and Electronics
Engineers (IEEE), the Wi-Fi Alliance and the Federal Communications
Commission (FCC) (or its equivalent in other countries). So many regulatory bodies
are in on this because unlike an Ethernet switch, for example, a wireless AP
could really interfere with other radio functions if it did not stick to its allocated frequencies
and transmission strength. Imagine if you set up your AP and discovered
that you had just jammed all radio contact between an airport tower and the aircraft
it was controlling. That would be bad. It would be worse for the people on the
planes, though.
Unlicensed Radio Bands
WLANs operate in one of the unlicensed radio frequency bands under the regulation
of the FCC (or its equivalent in other countries). These bands are called
the Industrial, Scientific, Medical (ISM) and the Unlicensed National
Information Infrastructure (U-NII) bands. These bands are reserved for use by
low-power radio equipment that does not require a radio operator’s license to
use (some WLANs can be operated in the ISM band at much higher power if
the operator acquires a license). Table 8.1 lists the information of interest.
Frequency Bands, Names, and Related Standards
Frequency Band Name Application
900MHz ISM Older cordless phones, Global System for Mobile
Communications (GSM) cell phones
2.4GHz ISM 802.11, 802.11b, 802.11g, 802.11n WLANs
5GHz U-NII 802.11a, 802.11n WLANs
802.11
The core WLAN standard is IEEE 802.11, sometimes known as Wi-Fi because
this was the first standard championed by the Wi-Fi Alliance. Wi-Fi is short for
Wireless Fidelity, a retro/hip reference to Hi-Fi. The IEEE ratified 802.11 in 1997.
In much the same way that Ethernet was standardized by 802.3 with subsequent
iterations of improved Ethernet getting extra letters to distinguish them from
the original (such as 802.3u, 802.3z, 802.3ae, and so on), the subsequent variations
and improvements to 802.11 are distinguished by a letter as well. The ones
you want to remember are 802.11a, 802.11b, and 802.11g. There are a couple
others in the works; you have probably seen 802.11n gear in stores. The
The WLAN standards you should know, and some of the relevant info
about each. (Some of the terms and acronyms will be explained in later sections.)
WLAN Standards (North American Version)
Characteristic 802.11 802.11a 802.11b 802.11g 802.11n
Date of Standard
1997 1999 1999 2003 2008?Max Speed (DSSS)
n/a11-Mbps FHSS n/a 11Mbps n/a 11Mbps per
stream
Max Speed (OFDM)
n/a 54Mbps n/a 54Mbps 600MbpsAssigned Frequency Band
2.4GHz 5GHz 2.4GHz 2.4GHz 2.4 and/or5.0GHz
Available Channels
11 23 11 11 11 or 23Approx. Range
75 feet 75 feet 150 feet 150 feet 500 feet
802.11, sometimes known as
legacy, specifies an 11Mbps maximum speed, using11 channels in the 2.4GHz band. The 11 channels available were used in a random,
rapid sequence to statistically avoid interference from other devices using
the same frequencies. This “skipping around” the channels is called Frequency
Hopping Spread Spectrum (FHSS). In reality, a lot of the data was lost to interference
anyway, and a more sophisticated system was engineered for 802.11a.
802.11a
802.11a uses a much higher frequency (5GHz) and a fancy method of using the
available channels, called Orthogonal Frequency Division Multiplexing
(OFDM). The science of how OFDM works is well beyond the scope of this
exam, but you should know the term and which standards it applies to. A big
advantage of the 5GHz band is that it is immune to common 2.4GHz emissions,
such as from cordless phones, baby monitors, microwave ovens, and many of the
wireless conveniences we take for granted that can really interfere with WLAN
transmissions in the 2.4GHz range. A disadvantage is that the higher frequencies
are more easily absorbed by structures and furniture, reducing the effective
range. However, the way OFDM works actually gives it a range advantage in
these office-type surroundings; in addition, higher frequencies mean smaller
antennas, which means we can increase the antenna gain (sort of like turning up
the listening volume). These things improve the range and so balance out the
range loss of the higher frequencies. It was mostly enterprise customers who
liked (and often still like) 802.11a, in part because it never caught on with the
general public so the risk of interference and security breaches was reduced.
On the topic of high and low frequencies and transmission range, here’s a little lesson to
help you remember what happens. Did you ever wonder why foghorns are really low notes,
instead of a shrill whistle? It’s because the low frequency travels much farther, especially
through fog, than a high one would. This is useful if you don’t want to drive your boat onto a
rock. For those who have never heard a foghorn, think of a car with a big stereo system: What
do you hear from a block away? Boooom… Boooom. Not the tweeters—the subwoofer. Low
frequency, longer range.
TIP
802.11b
802.11b, although later in the standards list, was actually in the market before
802.11a. 802.11b is back in the 2.4GHz range, so interference sources are a concern,
but now we have another method of using the available channels called
Direct Sequence Spread Spectrum (DSSS). Again, the complex science behind
how it works is not of concern for the CCNA exams, but you need to understand
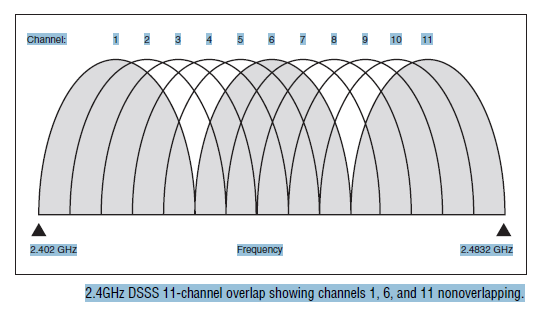
a little about it. There are eleven channels within the frequency band assigned
to this standard by the FCC. Typically, only three of these channels (channels 1,
6, and 11) are ever used because all 11 channels overlap each other. When two
APs use channels that are adjacent or close together (say, 2 and 3) or the APs
themselves are close enough together to “jam” each other, the signals from one
channel get stepped on, interfered with, and generally disrupted by the other.
Channels 1, 6, and 11 do not overlap each other.
2 3 4 5 6 7 8 9 10 11
2.4832 GHz
2.4GHz DSSS 11-channel overlap showing channels 1, 6, and 11 non-overlapping.
By sticking to these three channels, the frequencies are far enough apart that it
is very unlikely that they will interfere with each other, so less data is lost. In an
environment where you have multiple APs (as in most business implementations),
you take advantage of this by having your different access points using
different channels, consequently overlapping their coverage area without overlapping
the channels they use that could cause interference.
By sticking to these three channels, the frequencies are far enough apart that it
is very unlikely that they will interfere with each other, so less data is lost. In an
environment where you have multiple APs (as in most business implementations),
you take advantage of this by having your different access points using
different channels, consequently overlapping their coverage area without overlapping
the channels they use that could cause interference. We’ll mention this
again when we talk about BSS and ESS a little later.
802.11g
802.11g is currently the most popular standard, mostly because the home market
has significantly driven demand. Consumers wanted more speed and backward
compatibility with the wireless devices they already had, and they wanted it quickly
and cheaply, well before the standard was ratified. The home market exploded,
but the business market held back until that ratification happened to avoid deploying
immature technology (another reason that you will find more 802.11a than
802.11g in business environments). 802.11g is backward compatible with 802.11b
and uses the same 2.4GHz frequency band, but provides the same higher speeds
of 54Mbps and slightly longer range. This was a difficult engineering feat to
achieve, and if 802.11b and 802.11g do coexist in the same system, the 802.11b
tends to impair the performance of the 802.11g system. 802.11g uses OFDM for
most of its possible data speeds, but reverts to an 802.11b-compatible system for
others. Many wireless devices now provide a, b, and g capability in a single unit.
The problem with the popularity of 802.11g goes back to overcrowding and
interference. As I sit here in my home office, I can pick up no less than 12 wireless
APs, and all of them are using the same channel. Add in all the other interfering
devices in the 2.4GHz spectrum, and it’s a safe bet that these wireless
networks are providing less than optimal performance. A business-class WLAN
is expected to be of much higher quality than that, and the challenges of providing
that kind of quality are significant.
802.11n
802.11n, which at the time of this writing is not yet ratified by the
IEEE but is expected to be so in 2008, possibly as late as 2009. Manufacturers are
already selling “prestandard” 802.11n devices that comply with the draft standard,
which will presumably be upgradeable if the standard should substantially
change. The big draw is, of course, speed, with theoretical speeds of 600Mbps.
This opens up the exciting possibility of wirelessly streaming HD-format movies
from your media center to the TV in the bedroom without excessive delay. In
addition to OFDM and the use of the 5GHz band, 802.11n uses a feature called
Multiple Input Multiple Output (MIMO), which requires two sending antennae
and two receiving antennae, and allows for up to four send and four receive.
Effectively, you use multiple concurrent streams to achieve the high data rates.
That’s why the 802.11n APs often have several antennae on the box.
802.11n is exciting because it is fast, has great range, uses the 5GHz band
(reducing the interference and overcrowding problem) and is backward compatible
with a, b, and g. The only caution is that all of this is still prestandard; if you
are going to buy something, make sure the box at least says it is compliant with
the 802.11n draft standard.
WLAN Operational Modes
A wireless device can operate in either Ad Hoc mode or in Infrastructure mode.
The following sections describe these modes.
Ad Hoc Mode
Ad Hoc is Latin for “this purpose”; in this case, it refers to a connection between
wireless devices (such as two laptops, for example) for a temporary high-speed
link, perhaps to share files or play a game. No AP is required; indeed, no network
devices other than the two client machines are needed. Ad Hoc mode is
not usually associated with business-class networks.
Infrastructure Mode
In Infrastructure mode, an AP is required because the client devices cannot send
directly to each other; they must send through the AP. The AP, in turn, handles
all the wireless client data and provides the connection to the wired LAN by way
of its connection to the switch. Infrastructure mode is what you will find in business
environments. With the use of an AP, many devices can connect to the network,
and you can provide authentication and encryption for wireless
connections to help secure the WLAN.
Autonomous Mode
Within the Infrastructure mode of operation, Cisco makes a distinction between
Autonomous and Lightweight modes. The difference is simple: In Autonomous
mode, each AP is managed separately and sends wireless client data into the network
itself. This is a suitable mode for small networks where management and
security issues are not overwhelming.
Lightweight Mode
Cisco has put a lot of work into making WLANs manageable and secure. In
Lightweight mode, each AP associates with a WLAN controller, a special device
that provides a single point for management and security of multiple APs in the
network. The APs and WLAN controllers communicate using the Lightweight
Access Point Protocol (LWAPP), a Cisco-proprietary protocol built for this system.
In addition, all wireless client traffic from each AP is tunneled through the
WLAN controller. It’s more complicated and more expensive, but tremendously
powerful for managing and securing many APs in a centralized fashion.
Basic Service Set and Extended Service Set
Basic Service Set (BSS) and Extended Service Set (ESS) are terms that describe
how clients can associate with and use the available APs and network infrastructure.
The following sections describe these terms.
BSS
BSS is defined as a single AP that provides network connectivity for its associated
clients. You could have several APs in your system, but they would each be
offering a separate WLAN, and you could not “roam” between the APs; your
laptop would need to associate itself with each new AP when you lost signal
from the old one as you walked around the building.
ESS
ESS is more typical of a business environment. With ESS, each AP still defines
a BSS, but the group of APs and their BSSs form the ESS. The main advantage
is that clients can roam between the overlapping coverage areas of the individual
APs’ BSSs, without losing the functionality of their connection to the ESS
and thus to the network. To form an ESS, all the APs use the same Service Set
Identifier (SSID). An SSID is just a name (technically, it is a string of up to
32 alphanumeric characters) that identifies the WLAN. You might have three
APs for the office area, all configured with the same SSID, with overlapping
coverage areas. Each wireless client changes its association to the AP with the
strongest signal, which will change depending on where you are in the office and
where you move to. It is typical to have the APs use different channels, to reduce
interference and keep the throughput speed up. As you move, even though your
association to the BSS of the AP changes to that of the next one, your association
to the ESS provided by the three APs together does not, so your perception
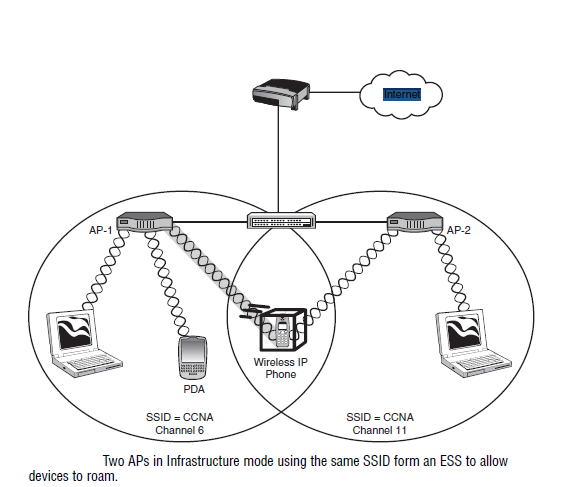
is that you never lose your connection to the network. Figure 8.2 shows what an
ESS system might look like; there are two APs, each using the same SSID but
on different channels. Mobile devices such as laptops, PDAs, or a wireless IP
Phone can move between the two APs without losing connectivity to the network.
In the diagram, the wireless IP Phone is roaming between the APs.
WLAN Security
This section takes a brief look at some of the security threats that target
WLANs and the methods available to mitigate those threats.
WLAN Security Threats
Any network is vulnerable to attack. A wired network requires that you physically
connect to a cable to execute an attack. If there is no possibility of an outside
connection to your wired system, an attack must come from an available
wired connection and is much easier to find and stop.
A WLAN’s versatility and convenience makes it a huge security vulnerability. By
adding an AP to your network, you are making it possible for people to connect
to your network without being in physical contact with it. The following are just
some of the more common WLAN threats that we need to guard against:
War driving
—Refers to driving around with a laptop, looking for unsecuredAPs to connect to and get free Internet access. Of those 12 APs in
my neighborhood, 4 of them are completely unsecured and I could connect,
use their Internet service, or snoop around their home network if I
chose to.
.
Hackers—Hackers usually want more than free Internet access; they arelooking for interesting or useful information such as credit card numbers
or other protected data, or else they just want to mess up someone’s network
out of malice or boredom. Being able to claim that they took down
Yahoo! for an hour gives them bragging rights; putting their former
employer offline is an act of revenge.
.
Internal—These attacks are the result of malicious or ignorant actions bythe company’s own employees. The classic example is the employee who
buys a little AP and plugs it into the network drop in their office. The
defaults on consumer APs are typically no security at all; now a hacker can
connect easily and steal access or information. The hacker does not even
need to actively seek information; the hacker can simply intercept the unencrypted
traffic and possibly get useful or private information. The FBI estimates
that more than 75% of network attacks come from internal sources.
.
Rogue APs—These are APs put in place in a WLAN without authorization.Usually, the hacker has spent some time with easily available software
tools intercepting the signaling between existing APs and clients.
Even if there is some security in place, given enough time, weak authentication
and encryption can be cracked. After the hacker has the necessary
information, the hacker can set up a rogue AP with the correct SSID and
authentication keys. Clients then associate with the device, and now the
hacker has direct access to all the information coming through that AP.
These scenarios make a business network admin freak out. For quite a while,
businesses were not implementing WLANs because they knew that the lack of
security was a major issue.
WLAN Security Methods
There are three main ways to apply security to WLANs:
.
Authentication—Requires all clients connecting to an AP to providesome (hopefully secret) information called a
key to prove that they areauthorized to connect. Ideally, we want to use
mutual authentication, wherethe AP also has to prove to the client that it is a legitimate (that is, not
WLAN Security
rogue)
AP. Strong cryptography allows the exchange of proof of the correctkey without actually sending the key; this small mathematical miracle
means that hackers can’t simply intercept the key and use it to gain access.
.
Encryption—Applies a mathematical formula and a secret key to the rawdata, encrypting it into a stream of gibberish that only another device
with the correct key and decryption formula can unscramble. If hackers
intercept encrypted data, they are unlikely to be able to decrypt it without
the key. I didn’t say it was impossible—there are some weak encryption
schemes out there that can be cracked relatively quickly. The strong
encryption schemes are strong enough that it would take years to crack
them, at which point most data would no longer be worth the trouble.
.
Intrusion detection/intrusion prevention—These systems guardagainst unauthorized use of the WLAN. These systems are typically
implemented as part of a Lightweight architecture. One of my favorites
is a system that detects a new AP in the system, interrogates it, and causes
it to shut down if it is classified as a rogue AP. Cisco’s Structured
Wireless-Aware Network architecture (SWAN) includes several devices
and tools that improve the manageability and security of WLANs. Learn
more about SWAN at www.cisco.com/go/swan.
As usual, different vendors were keen to get their product to market and start
making money, so there were some nonstandardized security systems in place
before the standards came out, but things have settled down somewhat into a
fairly consistent and pretty secure standard that most vendors are supporting. It
goes without saying that if you do not actually apply the security, it is not secure!
WLAN Security Standards
WLAN security standards you need to know
WEP
The Wired Equivalent Privacy (WEP) standard was introduced as part of
802.11. WEP uses a static preshared key system, meaning that all the APs and
all the clients must have the same key string configured in order to authenticate
and transmit encrypted data. The problems with this are that it is an administrative
headache to change the keys, which means they don’t change often,
which is not good. On top of that, the encryption method used was pretty weak.
These factors meant that a hacker could intercept lots of authentication
attempts, with all the clients using the same key over and over, all of it using
weak encryption. From that point it is a pretty simple matter to crack the
encryption, read the data, or connect to the network at will.
Some additional (not part of the standard) features were introduced by manufacturers
to bolster the flaws in WEP. Most APs allow you to choose not to
broadcast the SSID, which means that a client wanting to connect must know
the SSID. This is not going to fool a serious hacker; it is still perfectly possible
to capture WLAN traffic and determine the SSID in use. Another supplementary
security feature was the capability to filter which Media Access Control
(MAC) addresses (of client wireless NICs) could connect to the AP. The premise
was that no two MACs are the same, so only a short list of authorized MACs
needed to be added to the APs list. Unfortunately, it is a trivial matter to change
the source MAC with software, so after we learn an authorized MAC, we can
pretend to be that MAC.
Because its security features really deter only honest people, WEP should not
be considered a viable security method in current WLAN deployments.
The Cisco Interim Solution
Being one of the major stakeholders in the success of wireless for enterprise customers,
Cisco worked out an interim set of solutions to the problems WEP had.
In cooperation with the Wi-Fi Alliance, Cisco utilized components of the IEEE
802.1x authentication protocol and its own Extensible Authentication Protocol
(EAP) to significantly increase WLAN security. The three key improvements
that Cisco’s solution offered were the following:
.
Dynamic key exchange—This system utilizes an elegant cryptographicsolution to the problem of keying. Instead of a preshared key that all
devices must be manually configured with (and that as a consequence seldom
changes), dynamic keying allows the key to be secretly agreed upon
by the devices themselves, without administrative effort beyond setting it
up. Cisco used a proprietary method of dynamic keying.
.
User authentication with 802.1x—This component leveraged an existingIEEE authentication scheme, requiring the user to supply a username/
password package when attempting to connect. This added another
layer of complexity to the task of hacking in, because somehow the username
and password had to be learned. 802.1x is quite difficult to circumvent
if it’s properly configured, but it is somewhat complex to set up.
.
Unique key per packet—With the use of dynamic keying, the encryptionkey could change with every packet sent, so that even if the hacker
figures out the key, all the hacker can read is that one packet. This operation
obviously adds significant overhead to packet processing, but processing
power was getting better and cheaper all the time, so the benefits
outweighed the drawbacks.
Basic WLAN Configuration Steps
WPA
Cisco was out of the gate fast with a hybrid of proprietary and standards-based
protocols to address WLAN security, because the IEEE standards ratification
process was slower than the market demand. While Cisco was doing their own
thing on their products, the Wi-Fi Alliance kept one eye on what the IEEE was
likely to implement, so that they weren’t too far off base when the standard did
come out, and put forth a WLAN industry-standard (in contrast to IEEE standard)
security scheme called Wi-Fi Protected Access (WPA).
WPA set the same basic goals as Cisco’s solution, but with differences in how it
was executed. Dynamic keying was achieved using the Temporal Key Integrity
Protocol (TKIP) standard. WPA does device authentication either with simple
preshared keying or 802.1x authentication. This worked well for both the consumer
and business markets because the typical consumer could not set up an
802.1x system, whereas most businesses could and wanted the extra security.
One other benefit of WPA was its sponsorship by the Wi-Fi Alliance, which had
proved that its certification program could guarantee that Wi-Fi–certified
devices would work together reliably.
802.11i/WPA2
In 2005, the IEEE ratified the 802.11i security standard, which included features
for dynamic keying, authentication, and very strong encryption using the
Advanced Encryption Standard (AES) algorithm. Although functionally similar
to the Cisco and WPA systems, 802.11i is not backward compatible, and provides
much stronger encryption.
The Wi-Fi Alliance continues to certify equipment for compliance with the
802.11i standard, but they call it WPA2. This continues the positive association
with the success of WPA in the minds of consumers and IT managers, but causes
some confusion as to whether they are two different standards. They aren’t.!!
Basic WLAN Configuration Steps
Installing a WLAN is relatively simple, but you should bear in mind the following
procedure:
The steps to implementing a WLAN are as follows:
1.
Verify the existing wired network—Check that Dynamic HostConfiguration Protocol (DHCP) is working and that the virtual LAN
(VLAN) assigned to the access port is configured as required. If a client
connected to the port that the AP will use can get an IP address and communicate
with other network resources, the AP should be able to as well.
2.
Install the first AP—Assign the AP an IP address and mask and a defaultgateway for management purposes. Connect to the switch access port
with a straight-through cable.
3.
Configure the wireless settings—Change the default SSID to somethingin accordance with your local security policy (typically
not the companyname or phone number). Enable the radio, but do not enable any security
yet. Choose which standard(s) the radio will support (802.11a/b/g).
Choose the channel the AP will use (check what channels are in use
nearby). Choose the transmit power setting.
4.
Install and configure one wireless client—Verify that it can connect.Many current operating systems and NIC software products will automatically
discover APs and connect to the strongest signal.
5.
Verify that the client works—In the absence of security configuration,the simplest way to check is to try to browse the Internet. If the client
does not function properly, check the following:
.
Is the AP close to the center of the area where the clients are?.
Is there an interference source close by (microwave, cordless phone,or the like)?
.
Is the AP or the client close to a large metal structure (filing cabinet,steel door, reinforced concrete wall, steel-stud wall, heating/cooling
duct)? If so, move it to an area free of metal.
.
Is the AP’s coverage area adequate to reach the client? Try movingcloser to the AP.
6.
Configure the desired security features on both AP and client (it’s recommendedto use the strongest available security method).
7.
Verify that the client can still connect to resources in the presence ofsecurity configuration.
The configuration of security is beyond the scope of the exam, but you should
understand the process: If it works without security but stops working when you
add security, the security configuration is the likely problem.
1. Which of the following frequency bands is used by 802.11a ?
❍ A. 2.4MHz
❍ B. 2.4GHz
❍ C. 5KHz
❍ D. 5GHz
2. Which of the following are true of WLAN standards?
❍ A. 802.11b uses DSSS to achieve speeds of 54Mbps
❍ B. 802.11b uses OFDM to achieve speeds of 11Mbps
❍ C. 802.11g uses only OFDM in the 5GHz range
❍ D. 802.11a uses only OFDM to achieve speeds of 54Mbps
3. You have been given an 802.11b-compliant AP to install in your location in San Jose,
California. Which three channels will you be able to use without interference due to
overlapping?
❍ A. a, b, g
❍ B. 21, 22, 23
❍ C. 1, 5, 10
❍ D. 1, 6, 11
4. You want to be able to walk around your production floor with a tablet PC, checking
inventory and order status on the database. The shop floor will need four APs to provide
adequate coverage area. What mode will allow you to stay wirelessly connected as
you move between the four APs?
❍ A. Ad Hoc
❍ B. 802.1q
❍ C. BSS
❍ D. ESL
❍ E. ESS
182
Chapter 8: Wireless LANs
5. Which of the following is not a security scheme for WLANs?
❍ A. WEP
❍ B. WPA
❍ C. 802.11i
❍ D. MIMO
6. True or False: Multiple APs in the same ESS WLAN should be in the same VLAN.
❍ A. True
❍ B. False
7. Which of the following could interfere with your AP’s transmissions?
❍ A. A large magnet nearby
❍ B. An AM radio nearby
❍ C. A baby monitor nearby
❍ D. A CDMA cell phone nearby
8. Which standards-based WLAN security scheme includes dynamic keying and strong
encryption using AES?
❍ A. WPA
❍ B. Cisco EAP/802.1x
❍ C. 802.1i
❍ D. 802.11i
9. What is a rogue AP?
❍ A. An AP that has a faulty component, causing it to “jam” other APs by transmitting
collision frames at maximum power
❍ B. An AP that can be easily moved to any location in the building
❍ C. An unauthorized AP that is installed to facilitate the capture of information
❍ D. An AP that does not follow the accepted WLAN standards, but uses proprietary
protocols instead
10. Which option will you configure last when setting up your AP?
❍ A. 802.11i settings
❍ B. IP address and Mask
❍ C. a/b/g mode
❍ D. SSID
Answers to Exam Prep Questions
183
Answers to Exam Prep Questions
1. Answer D is correct. 802.11a uses the 5GHz range, not 2.4GHz, and certainly not anything
in the MHz or KHz range!
2. Answer D is correct. Answer A is incorrect; 802.11b cannot send faster than 11Mbps.
Answer B is incorrect; 802.11b does not use OFDM. Answer C is incorrect; 802.11g
does not use the 5GHz band.
3. Answer D is correct. In North America, the regulatory agencies have allotted the nonoverlapping
channels 1, 6, and 11 for use by 802.11b APs. Answer A is wrong because
the channels are numbered, not lettered, and these letters refer to the 802.11 standards
as a way to trick you. Answers B and C are the wrong channels.
4. Answer E is correct. The Extended Service Set allows you to roam between APs with
the same SSID. Answer A is wrong; Ad Hoc refers to a client-to-client temporary connection.
Answer B is wrong; the 802.1q standard refers to a switch-trunking protocol.
Answer C is wrong; Basic Service Set does not allow roaming, it provides association
to a single AP with a unique SSID. Answer D is wrong; English as a Second Language
is of almost no use in allowing you to roam wirelessly.
5. Answer D is correct. Multiple Input Multiple Output is a feature of 802.1n APs that
increases the data rate. WEP, WPA, and 802.1i are all security schemes for WLANs.
6. True. Multiple APs should be in the same VLAN, which is determined by the switchport
setting on the access switch that the AP connects to.
7. Answer C is correct. Baby monitors often use the 2.4GHz band, as do many APs, and
could easily cause interference. Magnets do not themselves cause interference (an
electromagnet might, or a fixed magnet that is part of an energized speaker might). An
AM radio is just a receiver and will not cause interference (unless there is a faulty component
“leaking” EMR). CDMA cell phones are usually down in the 800 or 1900MHz
band and are not likely to interfere.
8. Answer D is correct. 802.11i defines a set of standard protocols for authentication,
dynamic key exchange, and encryption using AES. WPA does not use AES; Cisco’s
EAP/ 802.1x solution is not fully standards-based and does not use AES; 802.1i is a
distracter to fool you.
9. Answer C is correct. A rogue AP is usually put in place by a hacker or an inside facilitator
to capture information from clients that associate to it unknowingly. Answers A, B,
and D sound good, but are just wrong.
10. Answer A is correct. Security settings should be the last component you configure,
after you have ensured that the AP works properly without security applied. Answers B,
C, and D are all part of the steps to set up the AP for client testing without security